Dagstuhl-Seminar 21451
Managing Industrial Control Systems Security Risks for Cyber Insurance
( 07. Nov – 12. Nov, 2021 )
Permalink
Organisatoren
- Simon Dejung (SCOR - Zürich, CH)
- Mingyan Liu (University of Michigan - Ann Arbor, US)
- Arndt Lüder (Otto-von-Guericke-Universität Magdeburg, DE)
- Edgar Weippl (University of Vienna & SBA Research - Wien)
Kontakt
- Michael Gerke (für wissenschaftliche Fragen)
- Susanne Bach-Bernhard (für administrative Fragen)
Impacts
- Towards Design Patterns for Production Security : article in 2022 IEEE 27th International Conference on Emerging Technologies and Factory Automation (ETFA) - Hoffmann, David; Biffl, Stefan; Meixner, Kristof; Lüder, Arndt - Los Alamitos : IEEE, 2022. - 4 pp..
- QualSec : An Automated Quality-Driven Approach for Security Risk Identification in Cyber-Physical Production Systems : article - Eckhart, Matthias; Ekelhart, Andreas; Biffl, Stefan; Lüder, Arndt; Weippl, Edgar R. - Los Alamitos : IEEE, 2023. - 12 pp. - (IEEE Transactions on Industrial Informatics ; 19. 2023,4 : article).
Programm
Industrial control systems (ICSs), such as production systems or critical infrastructures, are an attractive target for cybercriminals, since attacks against these systems may cause severe physical damages/material damages (PD/MD), resulting in business interruption (BI) and loss of profit (LOP). Besides financial loss, cyber-attacks against ICSs can also harm human health or the environment. Thus, it is of utmost importance to manage cyber risks throughout the ICS’s lifecycle (i.e., engineering, operation, decommissioning), especially in light of the everincreasing threat level that is accompanied by the progressive digitization of industrial processes. However, asset owners may not be able to address security risks sufficiently, nor adequately quantify them in terms of their potential impact (physical and non-physical) and likelihood. A self-deceptive solution might be using insurance to transfer these risks and offload them from their balance sheet since the underlying problem remains unsolved. The reason for this is that the exposure for asset owners remains and mitigation measures may still not be implemented adequately while the insurance industry is onboarding unassessed risks and covering it often without premium and without managing the potential exposure of accumulated events. This Dagstuhl Seminar aims to provide an interdisciplinary forum to analyze and discuss open questions and current topics of research in this area in order to gain in-depth insights into the security risks of ICSs and the quantification thereof.
In this seminar, we will focus on the issues of managing security risks in the context of ICSs with special emphasis on the economic aspects relevant to (re)insurance companies. Since academics and industry experts from diverse fields are involved in this highly interdisciplinary topic, we start the seminar by discussing specific terminologies and concepts of participating disciplines. After establishing a common ground, we outline key issues and research questions from different perspectives (viz., computer science, automation engineering, actuarial science), which will be addressed in this 5-day seminar. In line with the overall theme of the seminar, these issues or questions will concentrate on cyber insurance aspects. For instance, consider the issue of cyber accumulation that reinsurers have to deal with. Malware can spread rapidly and infect ICSs around the globe, including critical infrastructures. If multiple reinsurers fail to cover the damages caused by such cyber epidemics, the insurance industry could collapse. To counter the threat of world-wide cyber catastrophes that can even have devastating effects on the economy, we will discuss attacker models necessary to launch large-scale cyber-attacks against multiple industrial plants as well as the quantification of such cyber threat scenarios.
Based on the identified issues or questions, the participants will be divided into small groups to discuss a specific set of topics. Furthermore, the participants are encouraged to change groups throughout the seminar to contribute with their expertise on various topics. Group discussions and short presentations given by participants are complemented by individual work time to provide participants the opportunity to reflect on the topics discussed. As we cherish the philosophy of Dagstuhl seminars, we want to provide an open, vibrant, and inspiring atmosphere.
 Simon Dejung, Mingyan Liu, Arndt Lüder, and Edgar Weippl
Simon Dejung, Mingyan Liu, Arndt Lüder, and Edgar Weippl
The security economics community has an ambivalent position on quantifying cyber risk: on the one hand, there is a long-standing interest in establishing cyber risk measurement, while on the other hand, relevant publications report contradictory results [7] or present models with insufficient evidence of validity [6]. As researchers remain cautious about the interpretation of modeling results, the insurance industry’s need for gaining a quantitative understanding of cyber risk is more critical than ever. A serious concern for insurers is that a large-scale cyberattack could result in significant claims arising from transferred security risks. Considering the adverse business implications of cyber-related high-impact, low-frequency events, it is necessary to estimate and control the potential exposure to such losses. Previous industry studies attempted to address this issue by proposing hypothetical worst-case scenarios involving power grids [8], ports [9], and other industrial applications [4]. Furthermore, several industry-led working groups conducted workshops to assess the plausibility, impact, and claim implications of potential ICS-related catastrophic loss events (cf., for instance, [10, 11, 5, 12]). However, it is still not fully understood how the peculiarities of ICSs, technological change in light of strategic initiatives (e.g., Industry 4.0 [3]), and the increasingly sophisticated nature of cyber-physical attacks influence the loss frequency and loss severity [1]. Moreover, a holistic consideration of cyber-physical risk featuring the complete ICS lifecycle calls for an interdisciplinary research approach [2].
Thus, the aim of this Dagstuhl seminar was to bring together different communities to foster research activities that advance the understanding of cyber risks pertaining to ICSs and associated insurance aspects. The concepts developed as part of this seminar are a result of interdisciplinary work conducted by academics and industry professionals, both junior and senior, from the fields of
(i)computer science,
(ii) automation engineering,
(iii) actuarial science, and
(iv) economics.
To address the issues outlined above, the purpose of the seminar was to make the first steps toward a probabilistic cyber catastrophe model that is tailored to the ICS domain. In particular, we planned to achieve the basis of an economic loss model that builds upon worst-case scenarios in which globally and simultaneously many industrial processes in critical infrastructure sectors (e.g., power, petrochemical, transport, logistics) are affected by cyber-attacks. Figure 1 visualizes possible components of such a model, which were discussed and challenged during the seminar. In the first phase, the scenario is formulated, fundamental assumptions are specified, and the theoretical basis of the statistical model is formed. After that, the model is calibrated with data obtained from various sources, such as loss databases or subject-matter experts. Finally, the model and its underlying assumptions are validated.
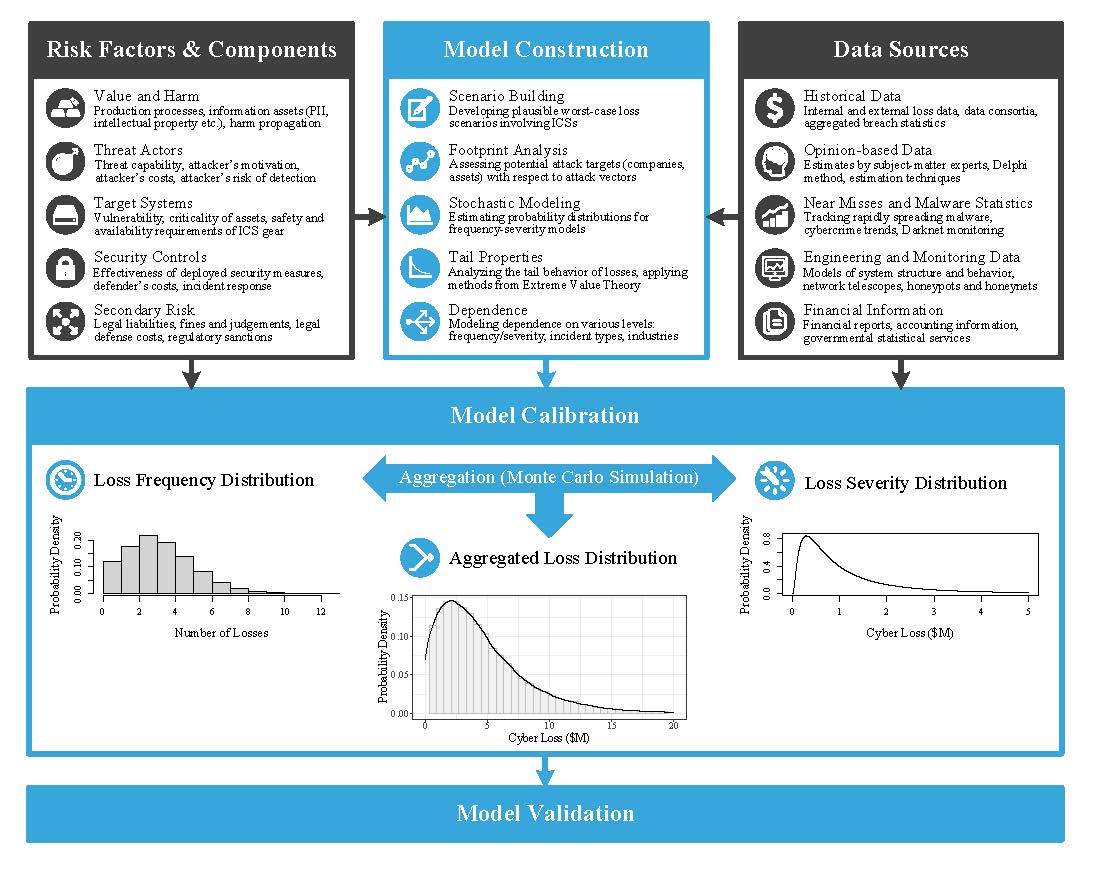
To set the frame for the seminar, the organizers defined four topics that were covered in plenary sessions and breakout sessions. In each plenary session, lightning talks were held that motivated the collaborative work in the breakout sessions. The working groups studied the same overarching topic of the breakout session (yet each with a different focus) in order to strengthen interdisciplinary exchange.
Overall, the following topics and motivating research questions were addressed:
- ICS Threat Landscape: How have cyber attacks against ICSs evolved and what should we expect in terms of attack sophistication, persistence, and impact in the future?
- Cyber-Physical Risk Quantification: How can we quantitatively model economic losses caused by ICS-focused cyber risks (i.e., probabilistic cyber catastrophe model)?
- Insurance: What are the opportunities and limitations of transferring ICS-focused cyber risks to insurers?
- Management of Security Risks: Which hard (e.g., technological security measures) and soft (e.g., information sharing, regulations, funding) factors increase or reduce the attack likelihood and severity?
The seminar started with a welcome session to bridge the disciplinary gap. In this session, the organizers presented the seminar program, explained key terms, and discussed core concepts to familiarize attendees with the terminologies used by different communities. Over the following days, several participants gave lightning talks that focused on the following topics:
- cyber-physical systems, security-relevant aspects within their lifecycle, and procurement considerations,
- current ICS security challenges with an emphasis on technological trends (e.g., Industry 4.0, smart manufacturing, Industrial Internet of Things),
- cyber-physical risk assessments, where special attention was given to analysis and quantification methods,
- various aspects of (cyber) insurance (e.g., cyber cat modeling, underwriting, economic problems, regulations), and
- security economics, featuring studies on cybercrime analysis and vulnerability forecasting.
The lightning talks gave participants the opportunity to present new perspectives and challenges, which led to lively discussions that shaped the group sessions. Unfortunately, the restrictions caused by the SARS-CoV-2 pandemic made it not possible to conduct the estimation exercises with all participants, which would have been required for achieving the cyber cat model. However, conducting the seminar in a hybrid format still enabled the participants both on-site and remote to work together on challenging open questions, contribute to group discussions, and forge new research collaborations.
The organizers thank all participants for their valuable contribution. Furthermore, this seminar would not have been possible without the great technical support provided by the Schloss Dagstuhl staff and the considerable effort made by the video conferencing assistants Sejdefa Ibisevic, Markus Maier, and Sara Tajik.
References
- Matthias Eckhart, Bernhard Brenner, Andreas Ekelhart, and Edgar Weippl. Quantitative security risk assessment for industrial control systems: Research opportunities and challenges. Journal of Internet Services and Information Security (JISIS), 9(3):52–73, August 2019.
- Gregory Falco, Martin Eling, Danielle Jablanski, Matthias Weber, Virginia Miller, Lawrence A. Gordon, Shaun Shuxun Wang, Joan Schmit, Russell Thomas, Mauro Elvedi, Thomas Maillart, Emy Donavan, Simon Dejung, Eric Durand, Franklin Nutter, Uzi Scheffer, Gil Arazi, Gilbert Ohana, and Herbert Lin. Cyber risk research impeded by disciplinary barriers. Science, 366(6469):1066–1069, 2019.
- Henning Kagermann, Johannes Helbig, Ariane Hellinger, and Wolfgang Wahlster. Recommendations for implementing the strategic initiative INDUSTRIE 4.0 – securing the future of german manufacturing industry. Final report of the Industrie 4.0 working group, acatech – National Academy of Science and Engineering, München, April 2013.
- Lloyd’s of London, Guy Carpenter, and CyberCube Analytics. Cyber risk: The emerging cyber threat to industrial control systems. Technical report, Lloyd’s of London, Guy Carpenter, and CyberCube Analytics, February 2021.
- Lobo, Francis. Upstream oil & gas cyber risk: Insurance technical review. Technical report, Joint Rig Committee, May 2018. A Joint Rig Committee Report.
- Vilhelm Verendel. Quantified security is a weak hypothesis: A critical survey of results and assumptions. In Proceedings of the 2009 Workshop on New Security Paradigms Workshop, NSPW ’09, pages 37–50, New York, NY, USA, 2009. ACM.
- Daniel W.Woods and Rainer Böhme. SoK: Quantifying cyber risk. In 2021 IEEE Symposium on Security and Privacy (SP), pages 211–228, May 2021.
- Lloyd’s of London and Cambridge Centre for Risk Studies. Business blackout: The insurance implications of a cyber attack on the us power grid. Technical report, Lloyd’s of London and Cambridge Centre for Risk Studies, July 2015.
- Lloyd’s of London, Cambridge Centre for Risk Studies, and Nanyang Technological University. Shen attack: Cyber risk in asia pacific ports. Technical report, Lloyd’s of London, Cambridge Centre for Risk Studies, and Nanyang Technological University, 2019.
- Dejung, Simon. Economic impact of cyber accumulation scenarios. Technical report, SCOR Global P&C, 2017.
- Dejung, Simon. Newsletter – risk assessment for ICS/SCADA security in industrial property, engineering, power, oil & gas. Technical report, SCOR Global P&C, March 2018. A joint workshop in March 2018 by LMA, IMIA & OPERA at SCOR (Zurich).
- IMIA Working Group. Cyber risks: Engineering insurers perspective. Technical Report 98 (16), September 2016. IMIA Annual Conference 2016 – Doha, Qatar.
 Matthias Eckhart, Simon Dejung, Mingyan Liu, Arndt Lüder, and Edgar Weippl
Matthias Eckhart, Simon Dejung, Mingyan Liu, Arndt Lüder, and Edgar Weippl
- Luca Allodi (TU Eindhoven, NL) [dblp]
- Gergely Biczók (Budapest University of Technology & Economics, HU) [dblp]
- Rainer Böhme (Universität Innsbruck, AT) [dblp]
- Carl Denis (Universität der Bundeswehr - München, DE) [dblp]
- Matthias Eckhart (SBA Research - Wien, AT) [dblp]
- Alexander Horch (HIMA - Brühl, DE) [dblp]
- Sejdefa Ibisevic (Universität Wien, AT)
- Julia Kittel (FH Emden, DE) [dblp]
- Klaus Kursawe (GridSec - Geneva, CH) [dblp]
- Arndt Lüder (Otto-von-Guericke-Universität Magdeburg, DE) [dblp]
- Fabio Massacci (Vrije Universiteit Amsterdam, NL) [dblp]
- Thomas Steinhaus (Munich Re, DE)
- Edgar Weippl (University of Vienna & SBA Research - Wien) [dblp]
- Jens Wiesner (BSI - Bonn, DE)
- Daniel Woods (Universität Innsbruck, AT) [dblp]
- Fabrizio Baiardi (University of Pisa, IT) [dblp]
- Vivien Bilquez (Zurich Insurance Group, CH)
- Achim D. Brucker (University of Exeter, GB) [dblp]
- Richard Clayton (University of Cambridge, GB) [dblp]
- Simon Dejung (SCOR - Zürich, CH)
- Andreas Ekelhart (SBA Research - Wien, AT) [dblp]
- Barbara Fila (IRISA - Rennes, FR) [dblp]
- Peter Hacker (Distinction.Global - Uetikon am See, CH)
- Teodore Iazikoff (SCOR - Paris, FR)
- Helge Janicke (Cyber Security CRS - Joondalup, AU) [dblp]
- Ersin Kaplan (HDI Global SE - Hannover, DE)
- Marina Krotofil (Maersk - Aarhus, DK) [dblp]
- Éireann Leverett (University of Cambridge, GB) [dblp]
- Mingyan Liu (University of Michigan - Ann Arbor, US) [dblp]
- Markus Maier (Universität Wien, AT)
- Jürgen Musil (Netinsurer - Wien, AT)
- Simin Nadjm-Tehrani (Linköping University, SE) [dblp]
- Ranjan Pal (University of Michigan - Ann Arbor, US) [dblp]
- Keyun Ruan (Empty Labs Ltd. - London, GB) [dblp]
- Galina Schwartz (Cyber Blocks Inc. - Berkeley, US) [dblp]
- Sara Tajik (SBA Research - Wien, AT)
- Josephine Wolff (Tufts Universtity - Medford, US) [dblp]
- Gordon Woo (Risk Management Solutions - London, GB) [dblp]
- Quanyan Zhu (NYU - Brooklyn, US) [dblp]
Klassifikation
- security / cryptology
Schlagworte
- Security
- Production Systems Engineering
- SCADA & ICS
- Industry 4.0
- Risk Engineering & Management





 Creative Commons BY 3.0 DE
Creative Commons BY 3.0 DE
